In the past few months, cyber attacks on computer systems both in home offices and big businesses have been hit with savage ransomware attacks. The first attack was called Wannacry and crippled many systems worldwide, including some components of the UK system and the Australian Speed Camera network (A community service if you ask me!) Shortly after Wannacry came Petya and in the same fashion it too crippled international systems, holding data hostage until the ransom was paid. The good news is these kinds of attacks are mostly preventable and the steps in this guide will show you exactly how to reduce your risk of becoming a victim.

Other Ways you can Protect Yourself From Future Ransomware and Malware Attacks.
Most of the recent ransomware attacks exploited a vulnerability in Windows computers, a service called Server Message Block Version 1 (SMBv1) an outdated yet still installed part of Windows OS. If you are running the latest version of Windows this weakness has been patched, however, if you can’t update to a new version of Windows or you just want to be 100% sure, you can manually disable SMBv1 using a variety of different methods. Below are three different options you can use to turn off SMBv1 on your Windows computer.
Disable SMBv1 Protocol to Prevent Ransomware Attacks using Control Panel.
Using the control panel method is by far the easiest way to disable the SMBv1 Protocol. So to get started the first thing you will need to do is open the Control Panel, go to Programs then Programs and Features.
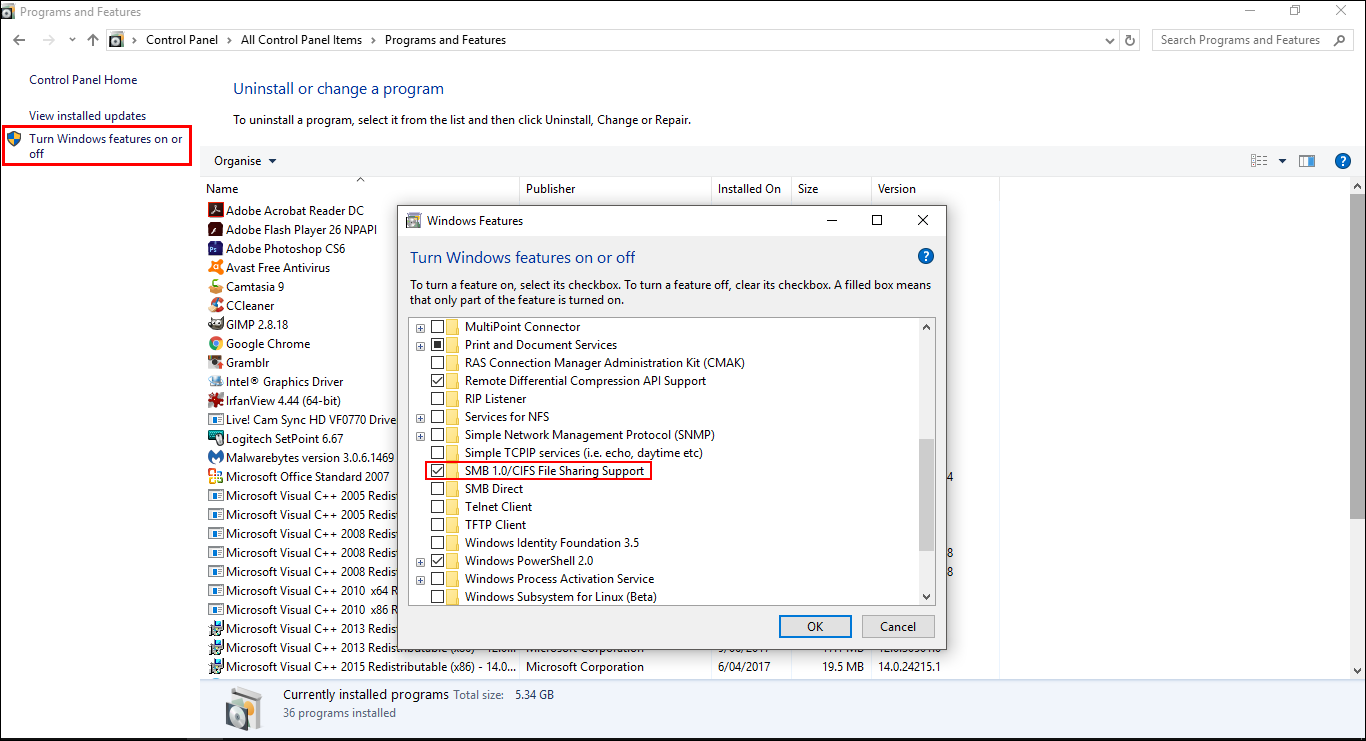
Once you have the Programs and Features section open, you will need to find Turn Windows features on or off which is located on the left-hand side of the window. When you find it, click it to open it. A new window will open showing a directory tree, on this list you will need to find a folder with the following name:
SMB 1.0 / CIFS File Sharing Support.
Note: It may have a slightly different name depending on your system version etc. However, the code will remain the same.
When you have found the folder, untick the box next to it and save your changes, it may take a minute or two to accept the changes and does require a restart. After the restart, your computer will no longer be able to be exploited using the SMBv1 security leak.
Disable SMBv1 Protocol to Prevent Ransomware Attacks using PowerShell.
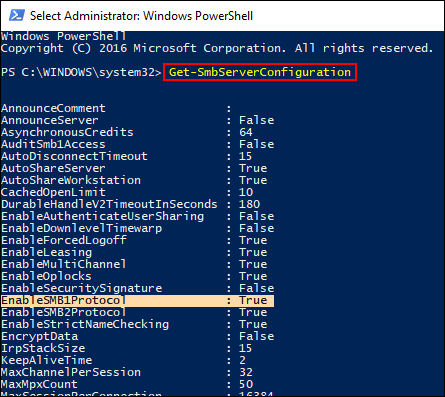
The second way you can disable the SMBv1 Protocol to prevent ransomware attacks is by using the PowerShell tool. This method is a little more complicated but still does the same job. To find the PowerShell tool, open your start menu and search PowerShell, when you have the blue PowerShell window open in front of you, you will need to enter the following commands, pressing Enter after each.
Get-SmbServerConfiguration
Set-SmbServerConfiguration -EnableSMB1Protocol $ false
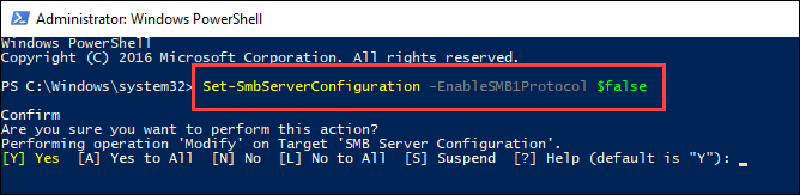
The moment the second command has been confirmed you will need to confirm the request. All you need to do is type Y into the window and press Enter once more. As soon as the command is finished you can close the PowerShell window.
If you ever wish to enable the option in the future all you need to do is Enter the below command into the Powershell tool:
Set - SmbServerConfiguration - EnableSMB1Protocol $ true
Disable SMBv1 Protocol to Prevent Ransomware Attacks using the Windows Registry Editor.
The third method you can use to disable the SMBv1 Protocol involves using the Windows registry, so it is important that before starting these steps, you have a Restore Point set. If you aren’t 100% sure how to create a restore point, open the start menu, type Restore, then select Create a Restore Point when it shows on the list. From the new window that appears click Create in the bottom right section of the screen, then follow the instructions given by Windows. Once you have successfully made a restore point you can continue with the steps below.
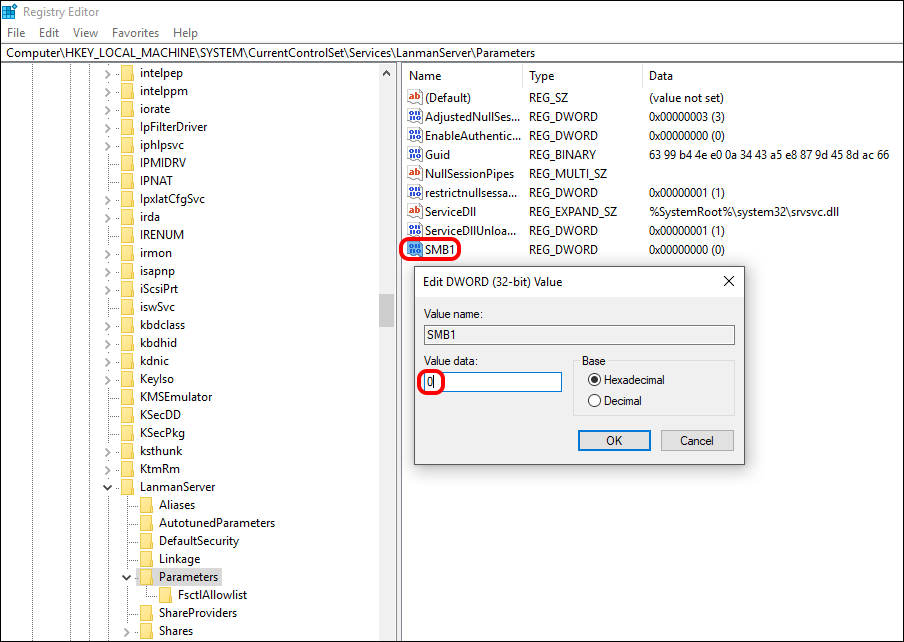
First, press Windows Key + R to open the Run tool and enter regedit into the window. Now using the left-hand pane navigate to the following location:
HKEY_LOCAL_MACHINE \ SYSTEM \ CurrentControlSet \ Services \ LanmanServer \ Parameters
Or just cut and paste the above address into the registry address bar. When you have selected the Parameters folder, you will need to right-click in the right pane window and select: New> DWORD Value (32-bit)
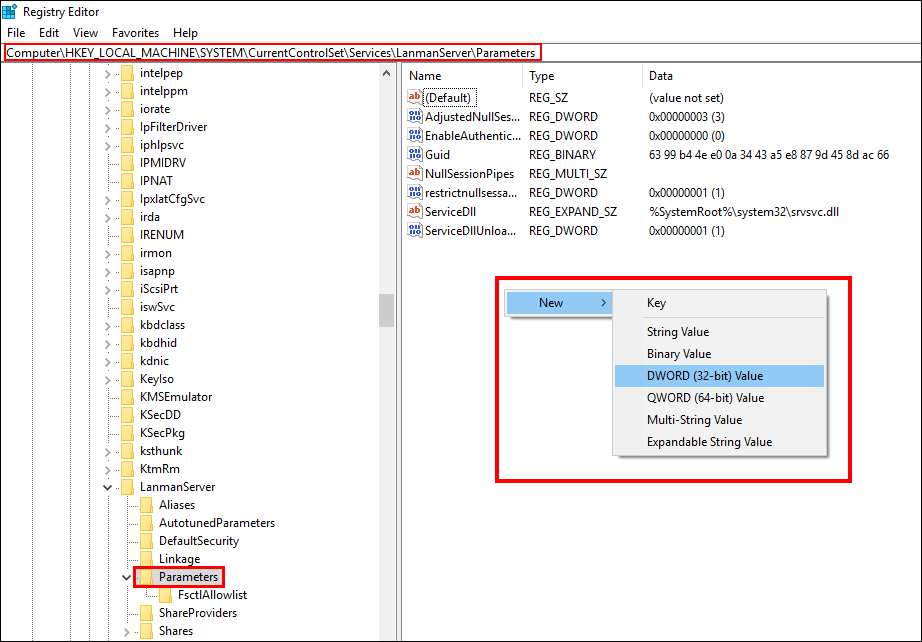
This will create a new file in the folder which you will need to name: SMB1. Once you have named the file, double-click on it and change the Value number to 0. Now all you need to do is click Ok and close the Registry. If you ever want to enable SMBv1 again all you need to do is go back to this newly created folder and change the 0 to a 1.
All three of these methods will allow you to disable SMBv1, preventing any possible Ransomware attacks using this exploit in the future. Personally, I would just use the Control Panel method as it is the easiest and you don’t have to worry about making any changes using the PowerShell tool or the registry editor.
