Table of Contents
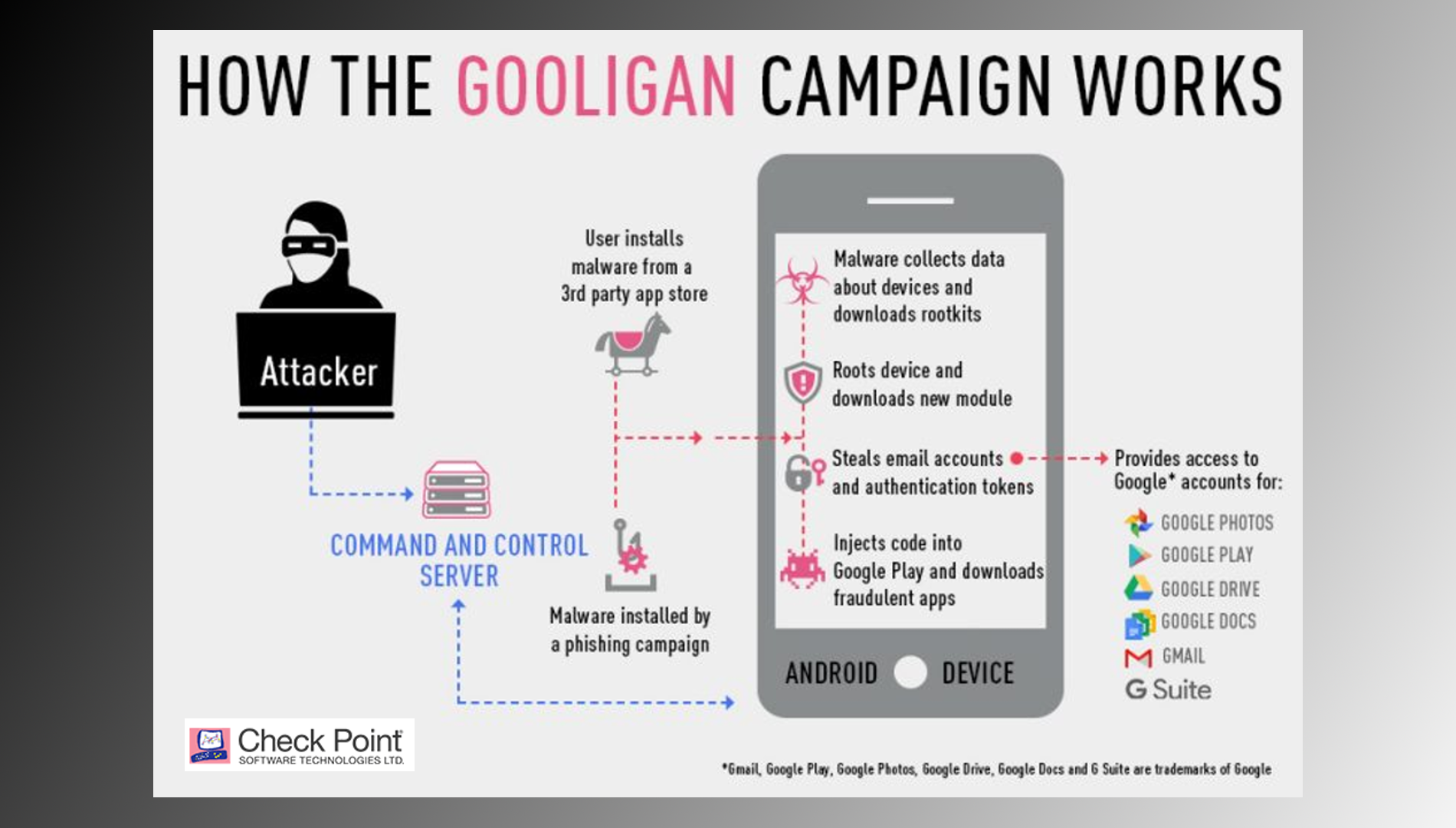
It seems that every week there is a new threat facing technology users, the latest instalment in this never-ending saga is a clever new malware campaign called Gooligan. Gooligan is generally spread via third-party app stores and the careless opening of emails, so follow closely and find out how you can limit your exposure with a few simple steps and some common sense.

How to fix Windows 10 Airplane/Flight Mode Internet Connection Issues.
Gooligan spreads in quite a similar manner to most other viruses and malware that are constantly floating around in the seemingly endless universe that is the internet. Android users can contract Gooligan quite easily when installing third party apps from unvetted, unofficial app stores or from links embedded within common phishing emails. Once your device has been infected, Gooligan uses authentication tokens stolen directly from you to steal your data from just about all of Google’s applications and services.
How Authentication Tokens Work.
Authorization tokens are issued by Google whenever a user logs into their account, so when stolen by a hacker or malware can be used to access all Google services for that specific username. Including Google Play, Gmail, Google Docs, Google Drive, and Google Photos. Even with Google’s two-factor-authentication enabled on an account, if the malware/hacker has stolen authorization tokens, it/they can completely bypass security, allowing hackers complete access to accounts.
Once Gooligan has acquired your data using the tokens it gathered, it will begin its malicious mission, installing adware onto your device and copying important data, usually passwords. This adware is how its creators generate revenue. Once on your system, Gooligan also uses your device and its newfound access, to further spread its reach by promoting other infected files and apps using positive reviews and ratings.
Note: Check Point has officially reached out to Google's Security team and is working closely with Google to investigate the source of Gooligan and fix any security flaws that may have allowed Gooligan access.
How to Check if You Have Been Infected With Gooligan Malware.
The official statement says that the Gooligan Malware only affects devices running Android 4.1 - Jelly Bean 4.4 - KitKat 5.0 Lollipop, which is a huge number of Android devices, more than 70% of all Android devices currently in use worldwide. If you have the ability to update your system past these versions, it is highly recommended. If you are worried about being infected, you can also check your device at checkpoints official website:
The Official Check Point Website.
Note: you can also find a list of apps at the above checkpoint website that are known to harbour Gooligan Malware.
What to Do if You Have Been Compromised By Gooligan.
If you have been unfortunate enough to be infected by Gooligan, the first and only real option is to completely wipe whatever Android device you have been using. Once your device has been wiped, you can begin a fresh new malware free install. After you have wiped your device fully, you will need to change your Google account password and login information, as well as every other password you have. You should also delete any and all emails that have come from senders you are unfamiliar with. As an added note, in future, you should learn to lean on the side of caution before opening any emails you think might be suspicious.
